How to fix CWE-23 Path Traversal vulnerability (Snyk)
CWE-23, or "Relative Path Traversal," is a common weakness enumeration (CWE) entry in the CWE/SANS Top 25 Most Dangerous Software Errors list. It is a type of security vulnerability that occurs when an application allows an attacker to manipulate the path used to access a file or directory. This can lead to unauthorized access to sensitive files or data on the system.
Here's how the CWE-23 vulnerability typically works:
- An application takes a file path as input from a user, often as part of a URL or a parameter in a web request.
- The application uses this input to construct a file path for file operations, such as reading or writing files.
- If the application doesn't properly validate and sanitize the input, an attacker can manipulate the path to access files or directories outside of the intended location.
For example, if an application uses a user-provided input like "../secret_file.txt" to construct a file path, an attacker could traverse up the directory structure and potentially access files or directories that should be restricted.
So in snyk security tool scan sometimes you can see the following error
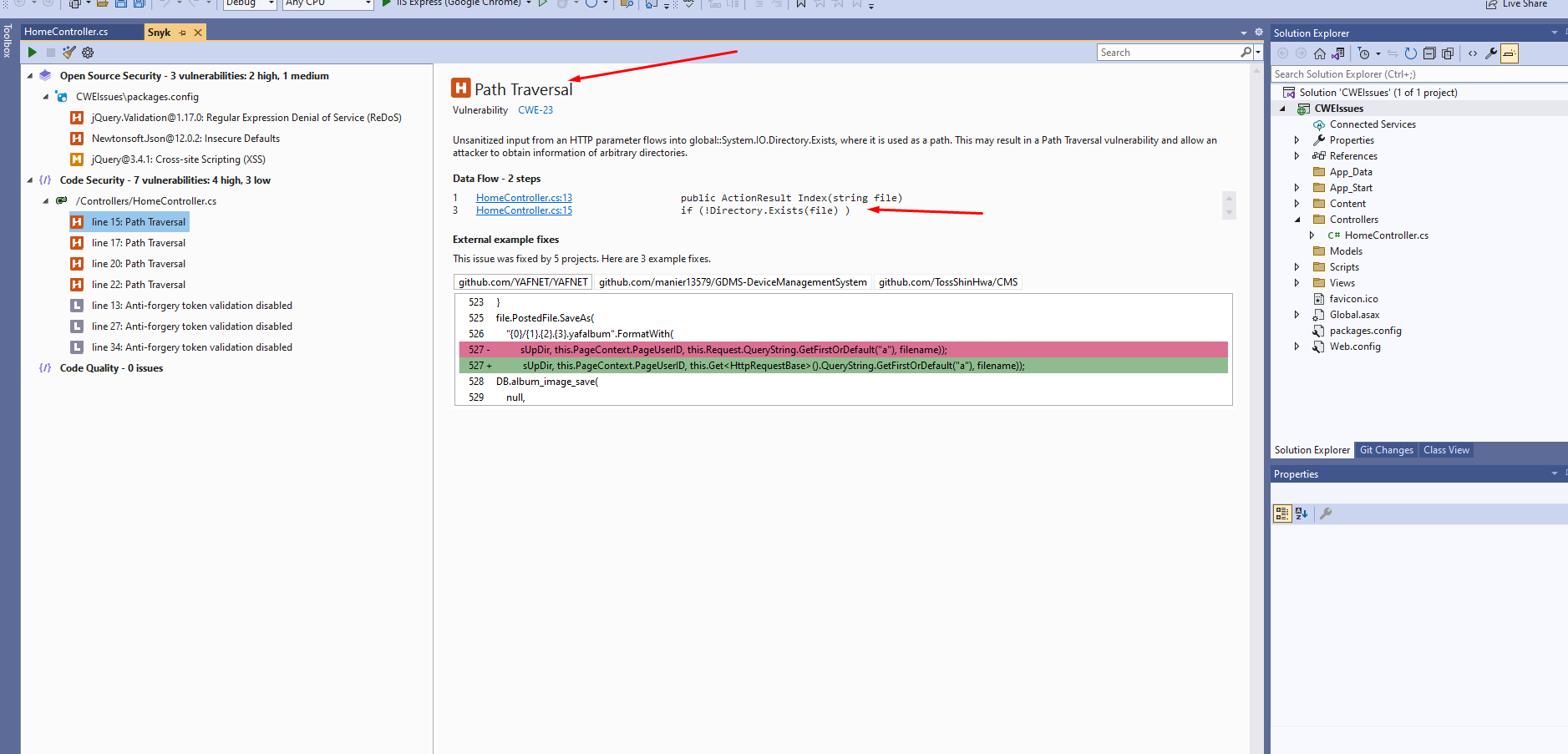
So for fixing this issue you have to replace the ".." with blank in the filepath
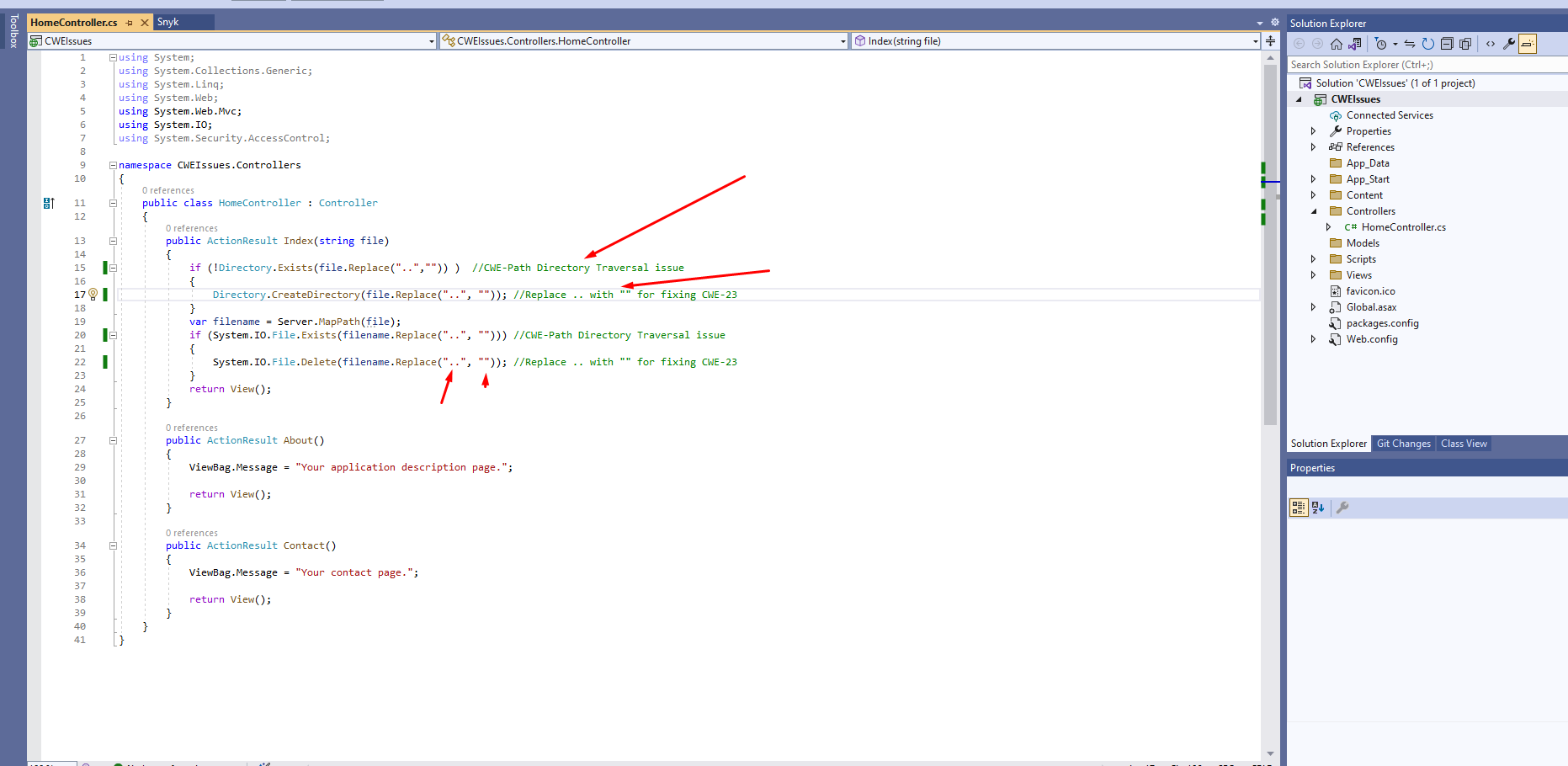
public ActionResult Index(string file)
{
if (!Directory.Exists(file.Replace("..","")) ) //CWE-Path Directory Traversal issue
{
Directory.CreateDirectory(file.Replace("..", "")); //Replace .. with "" for fixing CWE-23
}
var filename = Server.MapPath(file);
if (System.IO.File.Exists(filename.Replace("..", ""))) //CWE-Path Directory Traversal issue
{
System.IO.File.Delete(filename.Replace("..", "")); //Replace .. with "" for fixing CWE-23
}
return View();
}Now clean the scan result rescan the changes and you will see CWE-23 will be fixed in snyk security tool . You can notice the vulnerability count has dropped.
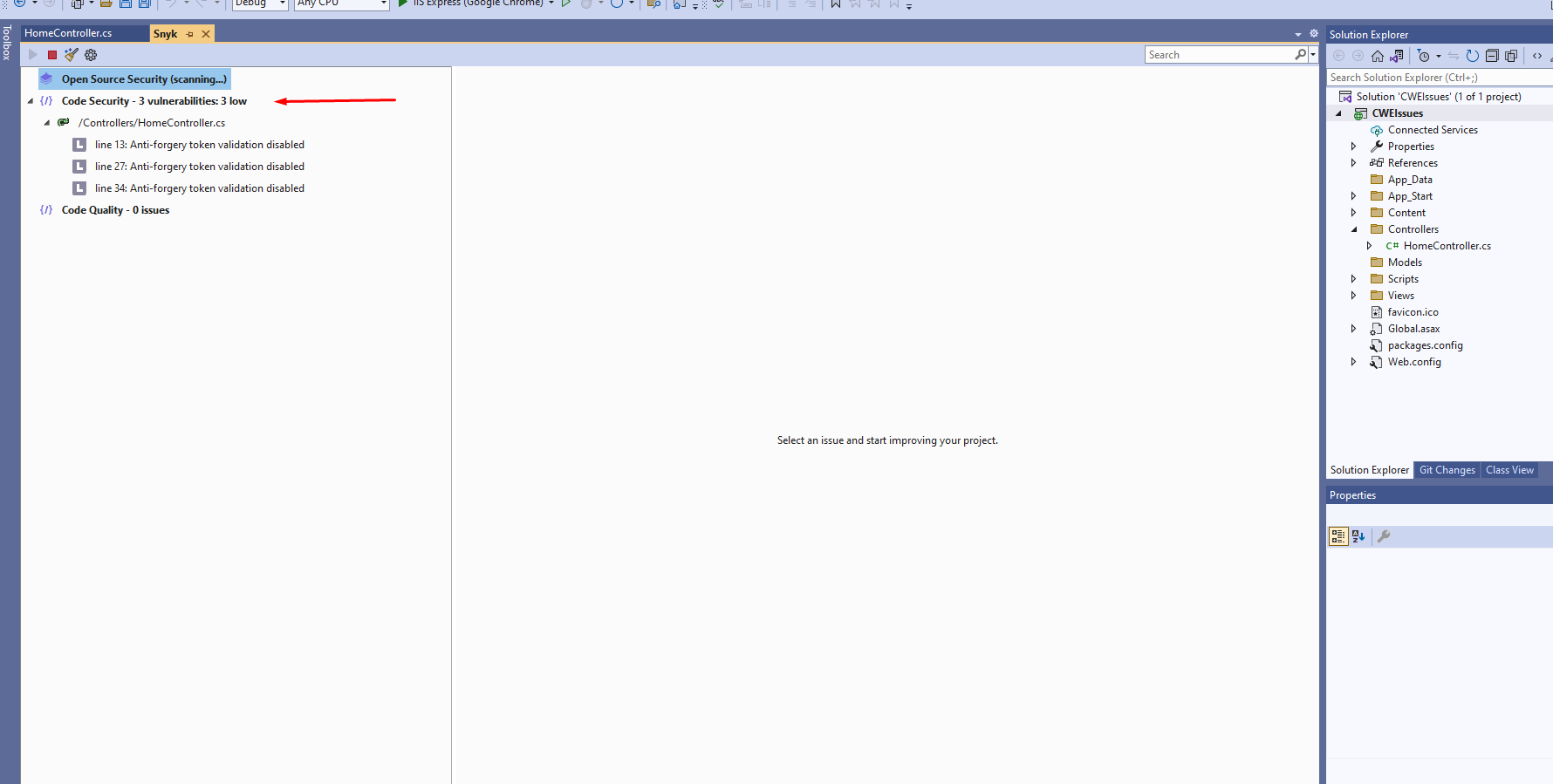
So this is how we can fix error CWE-23 Path Traversal vulnerability in Snyk Security scan tool in Asp.Net MVC.

